









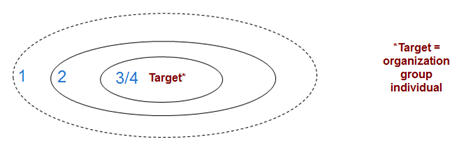
Types of Perpetrators
TYPE 1: A person with no legitimate relationship with the target. (OSHA “Criminal Intent Violence") TYPE 2: A person with a passing relationship, e.g., customer, vendor, or contractor of the organization or its employees. (OSHA "Customer/Client Violence") TYPE 3: A person with a significant relationship and intimate knowledge of the target, e.g., current or former employee, spouse/partner of an employee. (OSHA "Worker-on-Worker Violence") TYPE 4: Domestic/partner violence in the workplace. (OSHA "Personal Relationship Violence") OSHA and others have added Type 4, separating out personal relationships and domestic violence from Type 3. I view Types 3 and 4 as being operationally very similar when it comes to advanced threat mitigation strategies.Types of Threats
Direct Threats – straightforward and explicit statements of targeted violence, an intent to commit harm Veiled Threats – indirect, vague or subtle statements suggesting potential harm Conditional Threats – “if … then” statements of intent to harm and specifying conditions to be met in order to stop the threat or conditions under which the threat will be carried out Implausible Threats – statements of intended harm that are unrealistic and seemingly impossible to carry outThreat Potential Levels
Critical: on his way, in adjacent area or occurring now; critical incident/active shooter plan activated High: target, methodology and intent conveyed, imminent, a matter of when it will happen; law enforcement & security measures engaged Moderate: threat posturing, preparatory behaviors and/or rehearsal fantasies, significant risk factors present; mitigation/removal/isolation from site, security measures considered/engaged Low: grossly inappropriate behaviors, some risk factors present; active monitoring for escalation, plateau or de-escalation of behavioral trajectory Insignificant: inappropriate/immature behaviors, non-credible threats; passive monitoring for continued occurrences In reality, there is no such thing as “none” or “no” threat potential; we are one of the few species who will kill our own for ‘sport.’Threat Assessment for Targeted Violence
1. Threat posturing o Threat communicated ▪ Direct, indirect, conditional, implausible ▪ Verbal, written, text messages, social media postings o Hostile aggressive behaviors upon a person ▪ Verbal, physical ▪ Personal space intrusions, malicious glaring “maddogging” ▪ Hostile aggressive behaviors upon objects • Vandalism, destruction of property, throwing/breaking objects • Punching walls, pounding tables, slamming doors ▪ Is there a history of violent behaviors? • Have recent behaviors escalated in intensity, frequency and/or duration? o Has there been a narrowing of focus upon a target? 2. Preparatory behaviors o Investing time & resources towards a malicious act ▪ Researching & planning ▪ Checklists, recipes & “how-to’s” o Procurements ▪ Weapons, ammunition ▪ Supplies, equipment o Predatory behaviors ▪ Open source data searches of targets ▪ Surveillance o Probing & breaches ▪ Testing security & responses ▪ Timings & trial runs o Has there been a ramping up of behaviors? 3. Rehearsal fantasies o Obsessions & fixations with malicious themes o Recurring scripting of malicious acts o Repeated communications of what will transpire ▪ Leakage to a third party o Romanticizing past incidences of violence ▪ Active shooters & body counts o Costuming ▪ Omnipotent character ▪ Tactical gear o Legacy token ▪ Manifesto, video o Emotional/psychological investment into fantasies ▪ Increased risk of impelling one into action o Has there been a leakage of malicious intent?Restraining Orders & Forms
1 . Restraining Orders: General Information - Superior Court of California: County of Orange 2 . Workplace Violence Restraining Orders - California Courts, The Judicial Branch of California

A PRIMER ON THREAT ASSESSMENTS
Manny Tau, Psy.D., CTM

Manny Tau, Psy.D., CTM





Est. 1996 Manny Tau, Psy.D., CTM
CA Licensed Psychologist PSY14892
NoThreat.com

Clinical & Forensic Psychologist
Certified Threat Manager








